Programming as Theory Building: Why Senior Developers Are More Valuable Than Ever
In 1985, computer scientist Peter Naur wrote a prescient essay called “Programming as Theory Building” that feels more relevant today than ever.
Programming as Theory Building: Why Senior Developers Are More Valuable Than Ever
In 1985, computer scientist Peter Naur wrote a prescient essay called Programming as Theory Building that remains relevant today. The central thesis is that a program is not its source code; instead, ...
LinkedIn Announces Northguard and Xinfra: Scaling Beyond Kafka for Log Storage and Pub/Sub
LinkedIn today announced Northguard, a scalable log storage system that replaces Kafka, and Xinfra, a virtualized Pub/Sub layer. Northguard delivers sharded data & metadata, log striping, strong consi...
Can AI Replace Software Architects? I Put 4 LLMs to the Test
Will AI replace software engineers has been the quintessential question being asked in technology circles circa 2022 and beyond. The roles of product owners, graphic designers, and others shortly foll...
Can AI Replace Software Architects? Testing with 4 LLMs
Will AI replace software engineers has been the quintessential question being asked in technology circles circa 2022 and beyond. Today, I want to explore whether AI, particularly Large Language Models...
How I Make Better Architectural Decisions as a Senior Developer
Architectural decisions can make or break a software system. Making the right decision requires more than just technical skills - you need to weigh trade-offs, think about long-term effects, and colla...
Giving Voice to the Unbanked
DreamStart Labs (DSL) is a fintech with a social mission. Their main product, ‘DreamSave’, is a free app designed to simplify the management of savings groups in unbanked communities of developing cou...
Distributed TinyURL Architecture: How to handle 100K URLs per second
Rebrandly, a link management platform, developed a service that generated 100K URLs within a second. The solution helped its client, WonderCave, to raise millions of dollars in funds by sending SMS ca...
Automated architecture diagrams
Often an organisation’s technical systems have a complex dependency graph, which is not always easy to discover and reason about. And the biggest issue of all -> Are these diagrams still up to date...
InfoQ Software Architecture and Design Trends Report - 2025
Key Takeaways As large language models (LLMs) have become widely adopted, AI-related innovation is now focusing on finely-tuned small language models and agentic AI. Retrieval-augmented generation (RA...
How X (Twitter) Works: System Design for Billions of Tweets
Imagine this: You’re in a system design interview, and the interviewer leans in with a challenge. At first, it’s exciting — a dream project. But then it sinks in: billions of tweets, real-time feeds, ...
How to Build Idempotent APIs?
Why Idempotency is Important? Idempotency refers to the property of an operation where executing it multiple times has the same effect as executing it once. Distributed systems inherently deal with un...
Architecture Is a Conversation About Tradeoffs, Not Policing Templates
Every team wants the “right architecture.” So, we reach for the classics: layered, hexagonal, clean, microservices. Diagrams are drawn. Boundaries are named. And for a while, things feel solid.
Durable Execution: This Changes Everything | with Tom Wheeler

How would you code if your application could not fail? Consider how differently a senior engineer would approach the same project as someone just learning how to code. We can expect the neophyte to ...
3 Common Mistakes When Integrating OpenAI API with Your Web or Mobile App
A key concern when building a web or mobile application that uses OpenAI’s language models is protecting your private API key. Mistakes such as storing the API key in frontend code, using an unauthent...
Enterprise Access Control: ABAC vs RBAC in Service-Oriented Architectures
It was a quiet night in the city, around midnight on a weekday. I was part of the change team, and one of the few people on the office floor. This was of an Australian banks Identity and Access Manage...
Session Vs JWT: The Differences You May Not Know!
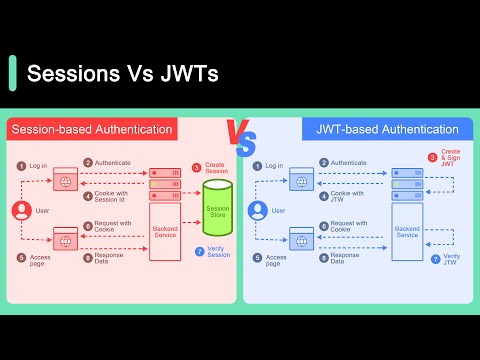
Get a Free System Design PDF with 158 pages by subscribing to our weekly newsletter: https://bit.ly/bytebytegoytTopic Animation tools: Adobe Illustrator and After Effects. Checkout our bestselling S...
Stop losing events: Microservice reliable message consumption
The world has changed. I see it in the water, I feel it in the earth, I smell it in the air. Much that once was is lost. From that ill-fated day onward, tickets bearing grim tidings that data had vani...
AT Protocol: Open, Decentralized Network for Social Applications
AT Protocol is an open, decentralized network for building social applications. Explore SDKs, quickstart guides for creating applications, self-hosting personal data servers, glossary of terms, and FA...
Architecture is a game of constraint satisfaction
In my Architect Elevator workshops, I often reference one of the many wise quotes by Eli Goldrat: Technology can bring benefits if, and only if, it diminishes a limitation. This insight has significan...
